In this article I will show how to configure firewall in linux using IPtables.
IPTABLES (FIREWALL):
SENDMAIL SMTP SERVER:
Purpose: A modular command based state-ful firewal.
Service Type: Standalone
Directory and File Location:
/sbin/iptables: Main iptables binary file.
/lib/iptables: iptables modules directory.
Required Packages:
iptables-version.number: Single package provides al modules and main iptables binary.
Prerequisite: IP packet forwarding should be enabled fist if your Linux box is acting as a
gateway for other PCs and you want to filter forwarded packets as wel.
Open “/etc/sysctl.conf” and set.
From
net.ipv4.ip_forward = 0
To
net.ipv4.ip_forward = 1
Save and exit and run folowing command.
sysctl –p
WHAT CAN IPTABLS DO?:
1. iptables can perform Static and Dynamic Filtering.
2. iptables can perform Quality of Service
3. iptables can perform Addres and Port Redirection
4. iptables can perform Nating
5. iptables can do much more by adding available modules.
STRUCTURE OF IPTABLES:
Iptables is consists of three tables
1. Filter Table
Filter table is used for blocking IP address and ports.
2. Nat Table
Nat table is used for Nating and Address and Port redirection
3. Mangle Table
Mangle is special purpose table used for QOS (quality of service) etc.
WORKING MECHANISM:
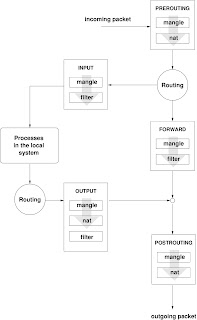
(Refer the image at the top of the article)
1. As soon as packets enters the system first PREROUTING is checked of MANGLE table and
then NAT table.
2. After that system checks its routing table and find out that if this packet is for itself or for
some other system (If system is acting as a network firewal and is a part of two networks,
normaly a system connected to internet).
3. If the packet’s destination is firewal system itself then INPUT chain of MANGLE table and
then INPUT chain of FILTER table is checked. And packet is given to concerned
service/process.
4. If packet’s destination is some other system and system has to forward this packet to
another system then:
a. FORWARD chain of MANGLE table and then FORWARD chain of FILTER table is
checked.
b. Then POSTROUTING chain of MANGLE table and then POSTROUTING chain of NAT table is checked.
5. If packet is generated by firewal itself then:
a. First routing decision is made first that packet wil go out using which interface. After routing decision OUTPUT chain of first MANGLE table then NAT table and finaly FILTER
table is checked.
b. Then POSTROUTING chain of MANGLE table then NAT table is checked.
RULES CREATION:
In iptables we have to create rules in chains to do a particular task.
iptables TABLE CHAIN CHECKING_CRITERIA ACTION
Example:
Folowing rule tels iptables to block FTP access from host 192.168.0.10
iptables –t filter –A INPUT –s 192.168.0.10 –p tcp –dport 20:21 –j DROP
Note: Filter table is default table of iptables if we do not specify any table in our rule then filter table is
assumed
Options Used in Rule Creation:
-A Defines the chain name to which the rule belongs to
-t Defines the table name to which the rule belongs to
-D To delete a single Rule
-F To Flush iptables al rules
-Z To set rule counters to zero
-n Do not resolve IPs to name from DNS used with –L option
-L Display curent firewal rules
-P To configure Policy Rule (default rule)
-p To define protocol (tcp, udp and icmp)
-s To define source address
-d To define destination addres
-o To define exit / out interface
-i To define incoming interface
-s-port To define source port
-d-port To define destination port
-m state –state To define status of packet
! To inverse the mentioned criteria
-j To define action to be taken on matched packet (DROP, ACCEPT, REJECT, MASQUERADE, and
REDIRECT)
COFIGURE IPTABLES AS A STATIC FIREWALL:
Scenario 1 (Filter Table, INPUT Chain Implementation):
End Result: A FTP server with firewal configured, ofering web services to only selected clients.
Server: linuxbox4 (192.168.0.14)
Alowed Clients: 192.168.0.15 and 192.168.0.16
Firewal Rules:
iptables –A INPUT –s 192.168.0.15 –p tcp –-d-port 20:21 –j ACCEPT
iptables –A INPUT –s 192.168.0.16 –p tcp –-d-port 20:21 –j ACCEPT
iptables –A INPUT –p tcp –port 20:21 –j DROP
Save Changes and set iptables service to start at boot time:
service iptables save
chkconfig iptables on
Scenario 2 (Filter Table, OUTPUT Chain Implementation):
End Result: A Client computer that is not alowed to telnet or SSH to a telnet and SSH server.
Server IP: linuxbox4 (192.168.0.14)
Firewal Rule Configured on Client PC:
iptables –A OUTPUT –d 192.168.0.14 –p tcp –-d-port 22:23 –j DROP
Save Changes and set iptables service to start at boot time:
service iptables save
chkconfig iptables on
Scenario 3 (Filter Table, FORWARD Chain Implementation):
End Result: A Gateway Server part of two networks (192.168.0.0 and 10.10.10.0) filtering incoming and
outgoing trafic only alowing 10.10.10.253 IP to acess file and print service on any PC in
192.168.0.0 network while not a single client PC in 192.168.0.0 network is alowed to acces
any service from 10.10.10.0 network.
Firewal Rule For Gateway Server:
iptables –A FORWARD –s 10.10.10.253 –p tcp –-d-port 135:139 –j ACCEPT
iptables –A FORWARD –s 10.10.10.253 –p tcp –-d-port 445 –j ACCEPT
iptables –A FORWARD –p tcp -d-port :1024 –j DROP
NAT CONFIGURATION / INTERNET SHARING:
Scenario 1 (Nat Table, POSTROUTING Chain Implementation):
End Result: An Internet gateway server converting internal private IP
addreses in to public IP addres.
Server: linuxbox4 (192.168.0.14)
Internet Clients: 192.168.0.0/24 Network
Server Interface Connected to Internet: Modem / Linux interface name ppp0
Firewal Rules:
iptables -t nat -A POSTROUTING -s 192.168.0.0/24 -j MASQUERADE
OR
iptables -t nat -A POSTROUTING –o ppp0 -j MASQUERADE
Note: -i option cannot be used with POSTROUTING CHAIN
For net sharing purpose you must complete the Prerequisite as mentioned at the beginning of this document.
PORT REDIRECTION (Used for T-Proxy Setup):
Scenario 1 (Nat Table, PREROUTING Chain Implementation):
End Result: A proxy server changing, destination port in incoming packets for T-Proxy.
Server: linuxbox4 (192.168.0.14)
Internet Clients: 192.168.0.0/24 Network
Server Interface Connected to Clients: NIC / Linux interface name eth0
Firewal Rules:
iptables -t nat -A PREROUTING -p tcp --dport 80 -s 192.168.0.0/24 -j REDIRECT --to-port 8080
OR
iptables -t nat -A PREROUTING -p tcp --dport 80 –i eth0 -j REDIRECT --to-port 8080
Note: -o option cannot be used with PREROUTING CHAIN
PRIORITIZE MSN TRAFFIC :
End Result: An Internet gateway server performing QOS MSN.
Server: linuxbox4 (192.168.0.14)
Alowed Clients: 192.168.0.0/24
Firewal Rules:
iptables -t mangle -A FORWARD –s 192.168.0.0/24 -p tcp -dport 1863 -j TOS -set-tos Minimize-Delay
This wil forward MSN trafic without delay and MSN service wil get improved.
DYNAMIC FIREWALL CONFIGURATION :
End Result: A FTP server with dynamic firewal configured, ofering web services to only selected clients.
Server: linuxbox4 (192.168.0.14)
Alowed Clients: 192.168.0.15 and 192.168.0.16
Firewal Rules:
iptables -A INPUT –s 192.168.0.15 -p tcp -dport 20:21 -m state -state NEW -j ACCEPT
iptables -A INPUT –s 192.168.0.16 -p tcp -dport 20:21 -m state -state NEW -j ACCEPT
iptables -A INPUT –s 192.168.0.16 -p tcp --dport 20:21 -m state -state ESTABLISHED,RELATED -j ACCEPT
iptables -A INPUT –s 192.168.0.16 -p tcp --dport 20:21 -m state-state ESTABLISHED,RELATED -j ACCEPT
iptables -A INPUT -p tcp -dport 20:21 -j DROP
Here:
-m state –state:
Is an iptables parameter, which is used to define a packet’s state.
NEW: NEW state means that the packet has started a new connection Such packets
has special TCP flag set in it (SYN)
ESTABLISHED: ESTABLISHED means that the packet is asociated with a connection that has
already been made by a NEW state packet.
RELATED: Means that the packet is starting a new connection, but is asociated with an
existing connection, such as an FTP data transfer, or an ICMP erorr.
INVALID: INVALID means that the packet is associated with an unknown connection.
Connection was not already created for this packets and neither this is an
associated packet with another connection.




No comments:
Post a Comment